Confidential computing is a privacy enhancing computing methodology intended to protecting data. The method isolates sensitive data during processing into a protected CPU enclave and only authorized programmers who have access to the contents of the enclave—the data that is being processed. The methods used to process it—and they are invisible and unknowable to anyone else, including the cloud provider.
Companies rely increasingly on public and hybrid cloud services, which makes it sure that data privacy is respected. The primary goal of confidential computing is to provide greater assurance to the leaders that their data in the cloud is protected and also confidential. This also encourages them to move more of their sensitive data and computing workloads to public cloud services. In order to protect data at rest (in storage and databases) and in transit (over a network connection), cloud providers have offered encryption services for years. By protecting data during processing or runtime, confidential computing eliminates the remaining data security vulnerability.
The Process of Confidential Computing
Normally we need to unencrypt data (in memory) before it can be processed by an app. This workflow makes the data vulnerable to memory dumps, root user compromises, and other malicious exploits. These exploits can take place before, during, and after data processing.
---
The technology behind Confidential Computing protects data in use by performing computations in a hardware-based trusted execution environment (TEE). A Trusted Execution Environment (TEE) provides a secure or trustworthy runtime environment for applications. A TEE can exist in isolation on a separate processor, directly on the main processor(s) of a computer system, or in a die of a multiprocessor system or a single-chip system (SoC). Only applications that have been specially activated for this purpose can be executed on the TEE. Depending on the manufacturer, there are different technologies for the realization of a TEE.
- AMD: Platform Security Processor (PSP), Secure Extension Mode (SEM), Secure Memory Encryption (SME)
- ARM: TrustZone
- Intel: Trusted Execution Technology (TXT), Intel Active Management Technology, Software Guard Extensions (SGX)
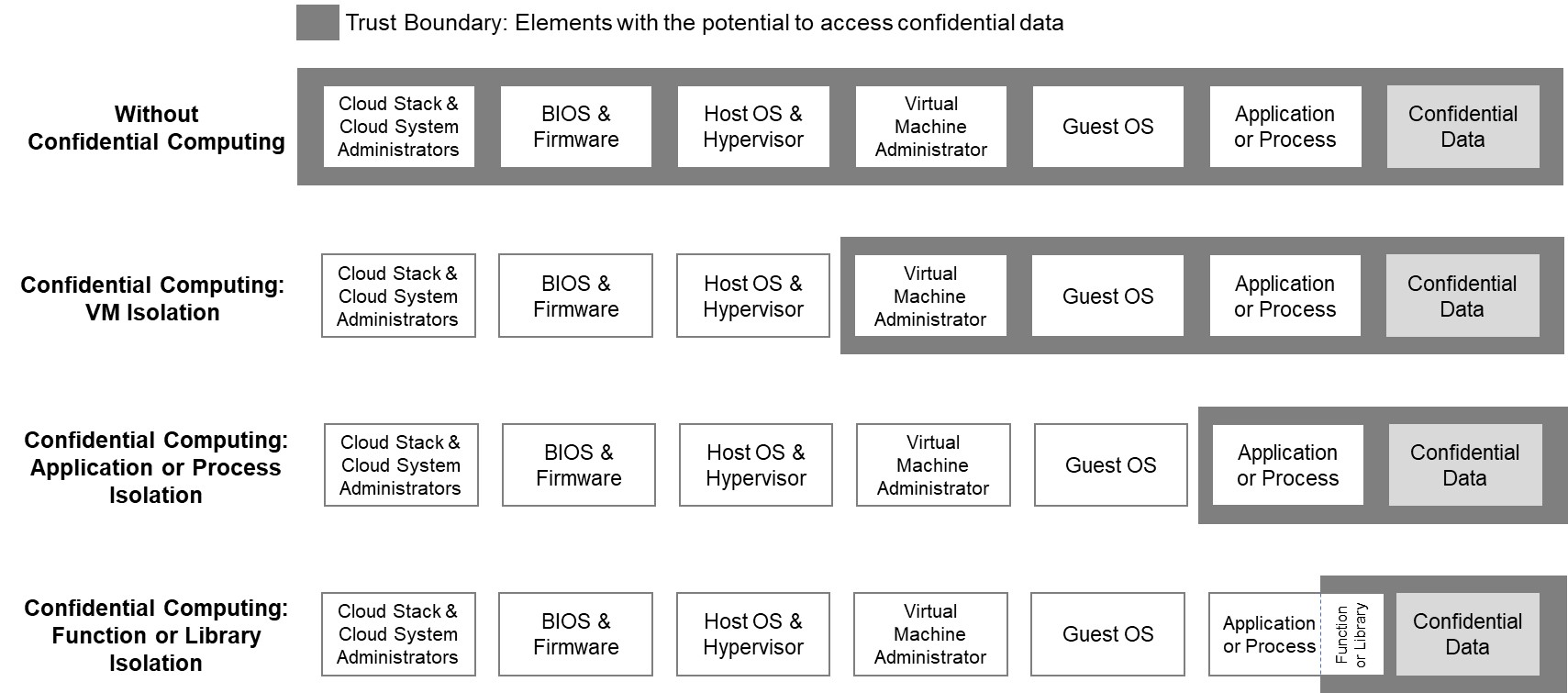
Diagram credit : Wikipedia
A hypervisor alone does not provide TEE. While it can run different operating systems on one processor, isolation is limited to the processor. A TEE also includes peripherals that can distinguish between access from secure and non-secure applications or operating systems.
Confidential computing leverages TEE. By using embedded encryption keys and embedded attestation mechanisms, the TEE is secured, ensuring that only authorized application code has access to the keys. In the event that malware attempts to access the keys — or if the authorized code is hacked or altered in any way — the TEE denies access and cancels the computation. This is how the sensitive data can be protected in memory till the app instructs the TEE to decrypt and proceed processing. In addition to TEE, remote cryptographic attestation is a part of confidential computing.
What are the Benefits of Confidential Computing?
Confidential computing and TEE can be used to protect various things which requires privacy such as business logic, analytics or some special applications. Today, TEE technology is mainly used on smartphones and tablets, e.g. for DRM. The further development and standardization of this technology is crucial for applications such as mobile banking and NFC payment options. The concept of Bring your own device (BYOD), the creation of a private area parallel to a secure area for company data, is also based on the TEE concept.
An edge computing framework brings enterprise applications closer to data sources like IoT devices or local edge servers in order to protect data processed at the edge. It is possible to protect data and applications at edge nodes with confidential computing when this framework of confidential computing will be used.